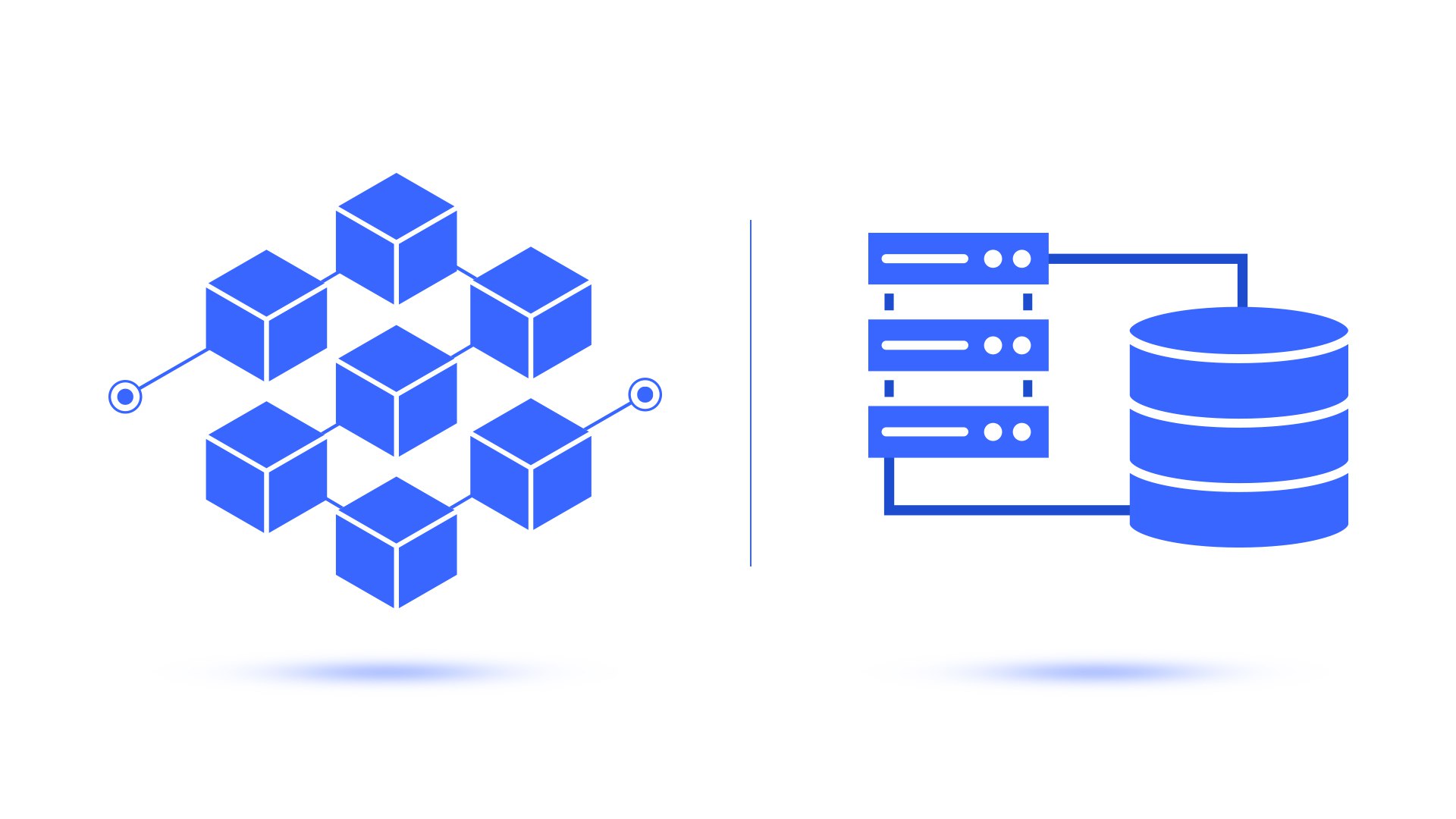
The blockchain is a decentralized and distributed ledger system capable of keeping records safe and transparent. It does not need to rely on a central authority. Traditional databases rely on a central authority to manage and validate transactions. Blockchain is basically based on decentralization, consensus, immutability, and transparency. Blockchain provides a persuasive opportunity for businesses exploring data management solutions.
So, how is blockchain different from traditional database models? Blockchain differs from traditional database models in many ways. In this article, we’ll clarify the key differences between these two models. We’ll also discuss the advantages of blockchain technology.
Basics of Blockchain Technology

There are two things to know. One is about blockchain fundamentals and the other is how blockchain works. Now, we’ll discuss these two things in a broad sense.
Blockchain Fundamentals
- Decentralization: In traditional systems, a central authority governs the entire network. Blockchain operates on a peer-to-peer (P2P) basis. This means that no single entity has control. It reduces the risk of a single point of failure.
- Transparency: Blockchain gives all participants in the network access to transaction history. It provides an open and shared ledger. All parties involved can confirm the legitimacy of transactions in blockchain technology.
- Immutability: Immutability is a key feature that differs blockchain from traditional databases. Once a block is added to the chain, it cannot be altered or deleted. This immutability is achieved through the cryptographic hashing method. Here, a chain of blocks is created where each block is linked to the previous one. This is a tamper-proof nature to ensure the integrity of the data.
How Blockchain Works
Blockchain works on some fascinating mechanisms. Such as:
- Blocks and Chains: Blockchain is named after its structure of linked blocks. All blocks contain a list of transactions. They are connected by a cryptographic hash. An unchangeable record of transactions is formed by this sequence of blocks. This chain is decentralized, so the network decides on transaction validity.
- Consensus Mechanisms: Network participants agree on transaction validity through consensus mechanisms. Popular consensus algorithms include Proof of Work (PoW) and Proof of Stake (PoS). PoW requires participants to solve complex mathematical puzzles to validate transactions. PoS transactions are validated by participants who possess a stake in the cryptocurrency. These mechanisms assure the blockchain only contains valid transactions.
- Smart Contracts: The terms of a smart contract are written straight into code. And the contract will carry out itself. These contracts automatically execute predefined rules under certain conditions. Smart contracts eliminate the need for intermediaries.
Traditional Database Models
Centralized Databases
Data administration has traditionally depended on centralized databases. Now, we’ll go through the characteristics of these databases. And it will become clearer about the challenges that they create.
Single Point of Failure
Centralized databases operate on a hierarchical structure. Here, a single authority controls and manages the entire dataset. This centralized control might seem efficient. But, it has a significant risk – a single point of failure. In case of central server failure, the entire database is at risk. This vulnerability threatens data integrity. Also, it can result in substantial downtime for businesses.
Limited Scalability
Centralized databases often face limitations in scalability. Centralized databases struggle to handle growing volumes of data and increasing user demands. The hierarchical structure of these databases makes workload distribution difficult. This leads to performance limitations and sluggish response times.
Data Manipulation Risks
The central authority manipulates and alters data in centralized databases. This control might be necessary for maintaining order. But at the same time it also opens the door to potential risks. Higher concerns include unauthorized entry, data tampering, and manipulation. Businesses using centralized databases must establish strong security measures to protect sensitive data.
Key Differences Between Blockchain and Traditional Database Models
Architecture
There are some structural disparities between blockchain and traditional databases.
Blockchain vs. Traditional Databases
| Feature | Blockchain | Traditional Databases |
|---|---|---|
| Control and Authority | Decentralized, no single controlling entity | Centralized, controlled by an authority |
| Data Distribution | Distributed across multiple nodes | Centralized on a single server |
| Immutability | Achieved through cryptographic hashes | Vulnerable to tampering and manipulation |
| Consensus Mechanism | Integral for reaching agreement on transactions | Relies on a central authority for validation |
| Scalability | Scales horizontally through distributed nodes | Often faces limitations in scaling horizontally due to hierarchical structure |
| Workload Distribution | Distributes workload efficiently across nodes | Centralized structure may lead to obstacles and performance issues |
| Performance | Generally more scalable for large-scale applications | Limited scalability for growing datasets and increased user demands |
Nodes and Peer-to-Peer Networks
Blockchain networks are made up of nodes that work with each other. It promotes collaboration without a central authority. Each node stores a copy of the entire ledger. This redundancy and fault tolerance.
In contrast, centralized databases rely on a single server or a cluster of servers controlled by an authority. They are not as redundant or collaborative as peer-to-peer networks.
Security
Blockchain and traditional databases employ different strategies to protect data.
Cryptographic Techniques in Blockchain
- Cryptographic Hashing: Blockchain uses cryptographic hashing techniques to secure data integrity. Each block contains a hash of the previous block. It creates a chain that is resistant to tampering.
- Public and Private Keys: Public-key cryptography ensures secure and private transactions. Participants have public and private keys. It adds an extra layer of authentication and authorization.
Vulnerabilities in Traditional Databases
- Single Point of Vulnerability: Centralized databases are vulnerable to a single point of failure. If the central server is compromised, the entire dataset is at risk.
- Limited Encryption: Traditional databases are centralized in nature. It makes them more vulnerable to data breaches and hackers, even with encryption.
Resilience Against Cyber Attacks
Blockchain is resilient to cyberattacks due to its decentralized nature. If one node is compromised, the overall integrity of the system remains intact.
Traditional/ centralized databases are often prime targets for cyber attacks. Because in this system valuable data is found in a single location. The consequences of a successful attack can be severe.
Use Cases

Blockchain Applications
- Cryptocurrencies: By using blockchain technology, cryptocurrencies were created. Bitcoin is the pioneer in this space. It proved that blockchain can be a safe, decentralized financial ledger. Cryptocurrencies use blockchain’s cryptography and decentralization to make digital transactions secure, transparent, and tamper-proof.
- Supply Chain Management: Supply chain management benefits from blockchain’s distributed ledger and transparency. Blockchain validates every transaction and movement from product manufacturing to distribution and delivery. Walmart uses blockchain technology to track the movement of their products. This technology improves traceability and prevents counterfeiting & fraud.
- Smart Contracts in Various Industries: Smart contracts are like self-executing agreements encoded straight into code. In real estate, they automate property transactions. In healthcare, they simplify patient data management. And in legal agreements, they ensure that predefined conditions are automatically carried out.
Database Applications
- Enterprise Resource Planning (ERP): Traditional databases play an important role in enterprise resource planning (ERP) systems. Inventory, procurement, finance, and HR are managed and organized using these databases.
- Customer Relationship Management (CRM): CRM systems rely on databases to store and manage customer-related information. Businesses can store client data in standard databases. This includes contact information, communication history, and purchase history.
- Data Warehousing: Data warehousing is storing and retrieving vast amounts of structured and unstructured data. Data warehousing relies on structured and organized databases, especially relational databases. These centralized databases simplify data management, query processing, and reporting in data warehousing applications.
Challenges and Considerations in Blockchain
Blockchain Challenges
Blockchain technology has many benefits. But there are also specific challenges to its widespread use.
- Scalability Issues: Blockchain provides a decentralized and transparent ledger. But scalability remains a significant challenge here. The network is under greater strain as the number of transactions increases. The consensus mechanisms and cryptographic hashing processes make blockchain secure. But they can also lead to slower transaction processing times. Developing scalable blockchain systems without compromising security is still a challenge for developers.
- Energy Consumption: Proof of Work (PoW) is a common consensus mechanism in blockchain networks. It requires significant computational power. This consumes a lot of energy and raises concerns about the environment. Alternative consensus processes like Proof of Stake (PoS) is trying to solve energy issues.
- Regulatory Hurdles: Blockchain’s decentralized nature challenges traditional regulatory systems. Governments and regulatory groups are still getting used to how blockchain is developing. This is leading to uncertainties in legal compliance. Balancing innovation and regulatory compliance is difficult. Especially in the context of cryptocurrencies and Initial Coin Offerings (ICOs).
Database Considerations
- Centralization Risks: Centralized databases provide efficiency and control. But they have their own risks. A single point of control makes them vulnerable to security breaches and unauthorized access. Valuable data in one location leads to data integrity risks.
- Data Integrity: Maintaining data integrity is an important consideration for any database. Traditional databases, especially centralized ones, can find it hard to maintain data consistency and accuracy. System failures, human errors, and malicious attacks can compromise data integrity.
- Security Measures: Security is a top priority in database management. Traditional databases implement security measures such as encryption and access controls. They are not immune to cyber threats. Regular updates, patches, and strong security protocols are essential to reduce risks.
Future Trends of Blockchain
Evolving Blockchain
Blockchain technology has great potential for future progress toward greater interoperability. Currently, many blockchain networks operate in isolation. This limits their potential. Interoperability will create an ecosystem where different blockchains can communicate and share data. Blockchain combined with Artificial Intelligence (AI), Internet of Things (IoT), and machine learning will revolutionize industries. Smart contracts may become more intelligent and adaptive with the integration of AI.
Scalability has been a persistent challenge for blockchain. But in the near future promising solutions are awaiting. Sharding, layer-two scaling solutions, and advancements in consensus mechanisms are tackling scalability concerns.
Database Innovations
Conclusion
Blockchain and traditional databases have different strengths and face distinct challenges. Blockchain’s decentralization, transparency, and security are incomparable. But challenges like scalability and regulatory concerns are still there.Traditional databases excel in structured data but face centralization and scalability difficulties. Businesses should compare industry needs versus technology strengths for an effective data strategy.